KL-7 rotor machine on the HMS Belfast
 I was recently in London and had chance to spend a few hours on board HMS Belfast, a retired British warship now serving as a floating museum on the Thames. The ship was pretty fascinating (that is, it had big guns), but my main motivation for visiting was to have a look at their KL-7 cipher machine. The KL-7 was an advanced NSA rotor machine design (think "souped-up Enigma") introduced in the 1950s and used within NATO.
I was recently in London and had chance to spend a few hours on board HMS Belfast, a retired British warship now serving as a floating museum on the Thames. The ship was pretty fascinating (that is, it had big guns), but my main motivation for visiting was to have a look at their KL-7 cipher machine. The KL-7 was an advanced NSA rotor machine design (think "souped-up Enigma") introduced in the 1950s and used within NATO. Although some details are still classified, quite a lot of information has emerged about how the machine worked. We (that is, the plebs with no security clearance) know that it used a scrambler consisting of 8 rotors, each with 36 contacts. It appears that some of the contacts were used in a "loopback" arrangement; that is, 10 of the contacts at the end of the scrambler were wired to 10 of the contacts at the start of the scrambler. This meant that the machine operated on a 26-letter alphabet, but that some outputs represented current which had passed several times through the scrambler. Here's a diagram of how this sort of thing works:
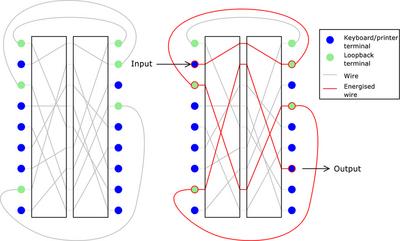
This feature would make cryptanalysis much more complex, as an attacker would have to take into account that an output could represent one, two, or more passes through the rotors.
One detail that's not yet known is precisely how the rotors stepped. We do know that one of the middle rotors was stationary during encipherment, and that each rotor had a detachable ring of plastic around its circumference with a series of bumpy bits. These operated microswitches to control the stepping.
While it was great to see a KL-7 exhibited on board the Belfast, I was a little miffed to find that it was poorly illuminated and, more damningly, that it was not even labelled.
Tags: KL-7 , Rotor machine , Cryptography

